Prosoft: Helping you navigate the modern IT security demands of HR systems
With the launch of Prosoft v9 in July 2021, 2022 was always going to be a challenging year for us, one of our key objectives for v9 was always to have a very customer-driven backlog, so listening to many new enterprise customers and watching their feedback shape the product has been a tremendously rewarding experience.
As we navigated discussions with our customers, we’ve identified recurring themes of security, compliance, and delivery. It’s obvious that every year that goes by brings with it an accelerating change in this space. Everyone has seen increased levels of pressure on CHROs and CIOs to deliver a secure space for their organisations' people data. What changed and how does it affect you?
1) Mandatory Payroll Vendor Statutory Submission
In Singapore, IRAS has announced the decommissioning of AIS offline applications (December 2022), a huge announcement as Singapore is one of the first countries in APAC to switch to submission via payroll vendor instead of direct manual submissions, and is often a leader in technology adoption soon followed by other countries in the region.
So why require companies to submit through payroll vendors?
- By pre-emptively putting vendors through a complex array of checks e.g., Security assessment and validation of specific payroll data cases, they can ensure that data is submitted correctly and securely.
- In direct contrast, a manual submission involves employees exporting huge amounts of confidential employee data into text files on local machines and submitting data through a website, a process that has any number of breaking points.
An important note here as these Payroll Vendor -> Internal Revenue Service interactions have become more common, they typically require the data to go from the Payroll Vendor to the Tax Agency, note I did not say “Payroll System”.
In the case of Singapore, Australia, and many governments undergoing such initiatives, the data has to go from the Payroll System to the Payroll Vendor to the Government Agency. Why is that important? It’s another nail in the coffin for legacy on-premise software. If your data has to go from On-Premise -> to Payroll Vendor Cloud -> to Government Agency, then it already means Cloud is mandatory within the ecosystem.
IT Departments that would simplify their compliance burden by going on-premise, no longer have that option, whether they like it or not, they will have to onboard 3rd party vendor cloud assets into the IT ecosystem. That’s a huge change for many companies.
2) Cloud, Microservices, and a new way of working
Another prominent topic that has come up with customers is security compliance, along with a general concern for how this topic is handled within the new distributed microservice system architecture.
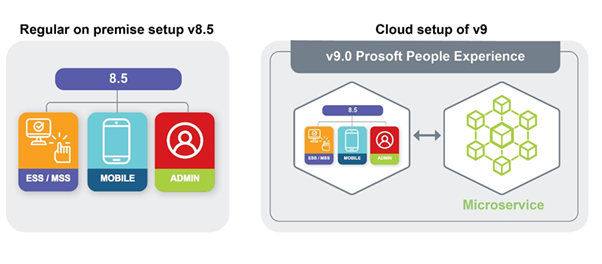
Our system has evolved quite a bit since the initial release of v9 in July 2022, but we can offer some insights into what has changed since that day.
- SOC2 - Unit4 achieved SOC2 compliance for our Azure Prosoft Service. SOC2 is the gold standard in security and compliance. Typically, when organisations send us security questionnaires, those questionnaires are heavily based on SOC2 requirements.
- Continuous Deployment / Continuous Scanning – As we leave behind the world of periodic deployments (Monthly Minor Releases, Quarterly Major Functionality Releases) and have moved into a world where code fixes can immediately be deployed independently of the monolith, our security practices have also changed. Security Scanning, which was a periodic activity, today is scanned in real-time prior to deployment into the cloud as soon as code is completed. Any changes that don’t pass inspection won’t make it to the cloud environment.
- Real-time code vulnerability assessment – Code scanning is great; it gives you confidence that the static code you roll out doesn’t have any basic security issues. But the new kid on the block in the security world is real-time code vulnerability assessment, where an agent sits on the cloud environment and interrogates not just the static code, but how customers interact with it; and it can give intelligent security recommendations based on that interaction. In layman’s terms, it’s almost like doing a penetration test on your service constantly.
We have always had great security practices, but the transition from v8/v8.5 to v9 is astonishing and we are super excited for other initiatives we have planned in the future.
3) The rise of real-time data
Organisations’ increased sensitivity on the topic of personal data security has given rise to a new age of real-time data. This has been further spurred on by companies investing in new technologies like corporate chatbots and natural language interfaces.
These may be somewhat rare now, especially in Asia for the corporate world, but we commonly see them today in our homes with technologies like Siri or Alexa. At Unit4 we are preparing for a future where these technologies will be ubiquitous within organisations. To that end, we are delivering:
- APIs for getting real-time employee data imported and exported
- APIs for common employee tasks, leave application, leave approval, reimbursements, etc.
That way, organisations can begin to hook their chatbots and internal systems into Prosoft directly and pave the way towards having a consolidated user experience.
Of course, the use cases of this API technology extend well beyond chatbots, as other simple examples are MNCs with global systems allowing their employees to apply for leave in Prosoft directly within the global HRIS and getting that employee real-time feedback (eg. Failed application). Our customers are already investing in low-code/no-code solutions that allow real-time data integration between Prosoft and various 3rd party systems.
Another example we are working on is the ability for the customers to extract statutory content and payslips safely from Prosoft and embed it directly in another system. A process that would traditionally involve clunky solutions like FTPS and exporting data for one system and importing data from the other system.
4) Why don’t we have a preview environment?
In recent years, we hear many customers ask this question why do we not have a preview environment? Why are releases sometimes in the 3rd week of the month right before payroll? These are all very valid questions. Part of our process that has made it difficult to execute on this namely the biggest challenge is that our 8.5 AWS infra has the test instance on the machine as production. With v9 hosting in Azure, one of the fundamentals of SOC2 is a strict separation of Production and Non-Production (Preview environments).
We are excited to announce that starting in Q4 2022, the target delivery of production will be in the first half of the month and of Non-Production/Preview environments will be approximately 2 weeks earlier. The full schedule of these dates will be announced on the Community4U website.
Some other minor changes that go along with this new process will be implemented as well, e.g., the publish of Release Notes in the admin module and users will be notified directly in the system if a maintenance window is coming.
In conclusion, it’s been a great year. Our product team and R&D team are on a mission day to day to take a great on-premise product, and turn it into a world-class SaaS first product with modern architecture. We are deeply appreciative of the customers that are onboard in that journey, supporting us and helping us to make the product better.